“Disclosures through Wikileaks did not contain any evident forgeries” (ODNI Report, p. 3)
The Office of the Director of National Intelligence (ODNI) released an unclassified report on the Russian hacking of the US election. The document is a consensus of the Federal Bureau of Investigation (FBI), the National Security Agency (NSA) and the Central Intelligence Agency (CIA). In some cases, there is a difference in expressed confidence between the agencies, with the NSA being less sure on some items. The intelligence community made no conclusions regarding whether or not the Russian efforts were effective in changing the result in the Presidential election of 2016.
The report details various actions that Russia takes to influence public opinion. There are a number of organizations mentioned in the report. These different organizations, according to the analysis, worked together in order to influence public opinion. These organizations are summarized in Figure 1.
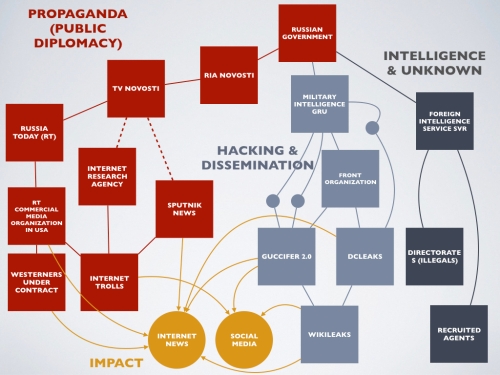
Figure 1 — Different organizations mentioned in the ODNI report on Russian interference in the 2016 Presidential Election. Note: The small dots are “cut-outs”; see discussion below.
We can divide the organizations into three categories: (1) propaganda and public diplomacy; (2) covert cyber activities (hacking and dissemination of information); and (3) intelligence collection and unknown covert activities.
Propaganda and Public Diplomacy
Russia Today. A very large amount of the report is dedicated to activities of the Russian government-sponsored news channel RT, which previously was known as “Russia Today”. It has a multi-layered structure. The RIA Novosti (РИА Новости) agency is the official news organ of the Russian government. It created a subsidiary TV Novosti (ТВ-Новости) to operate “autonomously” apart from the government. The word “novosti” in Russian means “news”. The root is “novo” which means “new”. (In English, the word “novel” as in “a novel idea” comes from the same root.) TV Novosti then created Russia Today (RT) as another autonomous organization. The intelligence assessment is that these organizations are not independent of the Russian government; that they follow the Kremlin “line”, and this is confirmed with quotes from the head of Russia Today.
Russia Today changed its name to “RT” because it was felt it would appeal to a larger audience. RT is the most frequently viewed foreign news channel in the United Kingdom. RT operates in the United States a commercial news entity as a stand-alone news organization. This organization then hires westerners to act as reporters. This is the multi-layered structure.
Sputnik News. Named after the world’s first satellite to orbit the earth, the technology that launched the “space race”, Sputnik News seems to have the same structure. The report is not clear if it is sponsored by TV Novosti or RIA Novosti or through some other mechanism. (In Figure 1, there are dotted lines indicating uncertainty.). Nevertheless, Sputnik news operates in a way similar to RT. There is also a Sputnik Radio network.
The important point is that both channels broadcast the opinions of the Kremlin. In other words, the report argues, they slant the news in ways that are not harmful to Russia. In addition, if Russia has enemies abroad, these enemies get damning critical coverage. News, therefore, is not journalism in the common sense of the news as theoretically found in the United States, but instead is viewed as being an instrument of state power.
These Russian entities operate somewhat like the Chinese XinHua, or the Voice of America, or France 24, or Radio France International (FRI), or the BBC, or Deutsche Welle. All of these are government sponsored news outlets.
Internet Research Agency. The report also mentions the Internet Research Agency, located in St. Petersburg here (formerly called Leningrad when the Soviet Union existed). This organization is said to deploy armies of Internet Trolls. In Russia, these are called “Web Brigades” (Веб-бригады). Trolls are persons who use assumed names to monitor news media websites as well as social media for the purpose of expressing opinions that follow the party line. For example, if it is decided that Hillary Clinton is not a favorite of Russia, then the trolls operate to insert negative Hillary comments in as many news outlets around the world as possible. Anyone who participates in online discussions through major news media web sites is familiar with this army of commentators. (Russia is not the only country to do this.)
Analysis of these Russian trolls shows a tendency to criticize anything about the United States that the Russian government does not like. According to the intelligence report, the overarching idea is to destroy the concept of liberal democracy.
Analysis. RT and Sputnik are the Russian version of similar government-supported news channels found elsewhere. They have been effective in getting their message across. In terms of the US election, it is not known how many Americans read Sputnik (probably not very many), or how many watch RT (compared to other media, probably not very many). Therefore, it is difficult to know if there was any substantial effect on the election. The Internet trolls may have had an effect, and may have been used to pump up and disseminate fake news, but no one seems to have measured this. After all, it is not possible definitively to identify the trolls.
Hacking & Dissemination by Russian Military Intelligence.
The GRU. The heart of the report concludes that the military foreign intelligence service of the Russian Federation, the GRU was responsible for hacking the emails from the Democrat party. GRU is an abbreviationn for Glavnoye Razvedyvatel’noye Upravleniye (Гла́вное разве́дывательное управле́ние). Glavnoye means Chief, or head. Razvedyvatel’noye means intelligence as in “collecting intelligence”. You can see the latin root “ved” which is “to see”. In English we have the same in the word “video”, from the Latin videre. In the United States, a rough equivalent to the GRU would be the Defense Intelligence Agency (DIA).
The report concludes that the GRU hacked the Democrat National Committee (DNC), took the emails, and also hacked John Podesta’s email account. So the next step was to deliver the information to the public, but without having anyone know it was sourced from the GRU. It is difficult to speculate on how the intelligence community identified the GRU as the source of the hacking. We do know, however, that intelligence collection on this type of operation within the United States would be done by the FBI, and intelligence collection outside the United States would be done by the CIA and for signals intelligence (SIGINT), by the NSA.
In terms of the National Security Agency (NSA), also known as “No Such Agency” or “Never Say Anything”, as far as the writer of this blog knows, this report on Russian hacking and influence operations is the first report ever published in the public with details of NSA assessments. Perhaps there have been others, but NSA does not usually publish anything at all except historical documents available through the National Cryptologic Museum, which is well worth the visit if you can find it.
Front Organizations. Sometimes covert operations (intelligence, police, industrial espionage teams, consultants) set up companies or organizations (non-profits, research services) to do certain work, but without identification of their true owner (sponsor, controller). The report does not specify any front organizations, but during the Cold War a number were used to shape international public opinion. Evidently the concept of front organization was invented by Vladimir Lenin in his 1902 manifesto “What Is To Be Done“. The list is long, but front organizations associated with the Cold War and even before include the International Confederation of Free Trade Unions, the World Federation of Trade Unions, the Women’s International Democratic Federation, the World Peace Council, the International Union of Students, the Pan-Pacific Trade Union Secretariat, the Japan Peace Committee (日本平和大会), the Society for German Soviet Friendship. There is no need to provide a complete list here. Guccifer 2.0. In this context, the report seems to express some suspicion that the hacker Guccifer 2.0 was a front organization. Rumored to be a single Romanian hacker, evidently it is not a single individual, according to the report. These things are murky. DCLeaks. This organization also was used as a conduit for providing information.
Cut-Outs. In Figure 1, the little circles represent “cut-outs”. The term “cut-out” is specific to espionage tradecraft, and represents a third party intermediary who can be trusted as a courier to transport information. Actually, one cut-out can pass the information to another before the information is given to the final destination. The utility in cut-outs is that their identities usually are vague. So if a source of information (S) hands the information to cut-out 1 (C1), who then hands it to the second cut-out (C2), who then hands it to the recipient (R), then (R) will not know the source of the information, and probably (C2) does not know the source of the information. And of course (R) is unaware of (c1) and so on. This system is made even more effective if the cut-outs have complete false identities, or if even their false identities are unknown to each other. (Even if interrogated, C2 would not be able to identify C1, and so on.)
False Flag Operations. This leads to the so-called “false flag” operation. False Flag is another espionage tradecraft term. It generally refers to a situation in which the person taking the action (whatever it is) thinks they are working for one country (or organization), when in actuality they are working for a different one. The use of cut-outs aids in getting people to provide their services (because they think they are working for someone else), but also aids the process of obscuring the source of any disseminated information.
Wikileaks. So when Julian Assange of Wikileaks says that he did not receive the information from a state party or a representative of a state party, he easily could be telling the truth, or at least the truth as he knows it. This doesn’t really matter, because once the information was released, the GRU had accomplished its purpose.
Intelligence and Unknown
SVR. The third type of operation mentioned briefly in the report is what we might call “classical espionage” conducted through the Russian Foreign Intelligence Service (SVR) Слу́жба вне́шней разве́дки (again you see the verb root “ved” in the last word, from the Latin videre). The report mentions use of Directorate S (Illegals). Illegals are another espionage tradecraft term that refers to persons inserted into a society, like the United States, under completely false identities, even pretending to be Americans. The popular television series “The Americans” is an example of “illegals”. It also mentions persons who are recruited by the SVR to carry out espionage work. There were little if any details provided, and no examples, except that the report indicates the SVR systematically collected information on the US election system, including information on State election commissions. The report indicates there is no evidence of hacking the polling machines or changing the vote counts.
Other Campaigns
Apart from the actions regarding the election of the 45th President of the United States, the report cites other campaigns, including a few that the Russians believe were directed at Russia. These include the Olympic doping scandal, and release of the Panama Papers. It also describes Russian activities in support of Occupy Wall Street, and campaigns that criticize American democracy as being corrupt and not representative of the people, and that convince people “the media” is providing them false information. The report also argues that RT specials with an anti-fracking message are designed to hinder development of a challenge to Gazprom, the giant Russian energy company that supplies natural gas.
Summing Up
The intelligence report describes a range of public opinion campaigns directed by the government of Russia. The major bombshell seems to be that the GRU is blamed for hacking the Podesta emails, and then through third parties getting the information to Wikileaks in a way that disguised the origin of the hack.
The remainder of the report describes programs of information (and “disinformation”) that have been in place since the Cold War.
The underlying message of the report is that the overall aim of the Russian campaigns should be seen in a larger context. It was not only to keep Hillary Clinton out of office, but to entirely discredit the democratic liberal order established by the United States in the Post War period. This includes spreading information that makes people believe the entire system is corrupt.
Trump’s Response
The 45th President has stated that although there is evidence a large number of countries hack into the United States, the Russian actions did not change the outcome of the US election. And to repeat, the intelligence report did not come to any conclusions in this regard.


